The rapid application of zero-day patches is crucial to prevent any vulnerability in the computer park. Moreover, vulnerabilities can affect all computers, as we have seen with the Print Nightmare exploit. With WUfB, find out how to quickly update your fleet when a patch is released.
What is a zero-day vulnerability?
A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit.
These vulnerabilities are discovered before security researchers and software developers are aware of them and deploy a patch. Zero-day vulnerabilities present a higher risk to users for the following reasons:
- Cybercriminals rush to exploit these vulnerabilities to their advantage.
- Vulnerable systems are exposed until a patch is released by the vendor.
Zero day vulnerabilities usually involve targeted attacks. However, many attacks still use older vulnerabilities.
Applying zero-day patches manually
To get the zero-day patches, an easy way is of course to go through WIndows Update. To do this:
- Open Settings.
- Go to Update and Security.
- Make sure you are on the Windows Update pane and click on Check for updates.
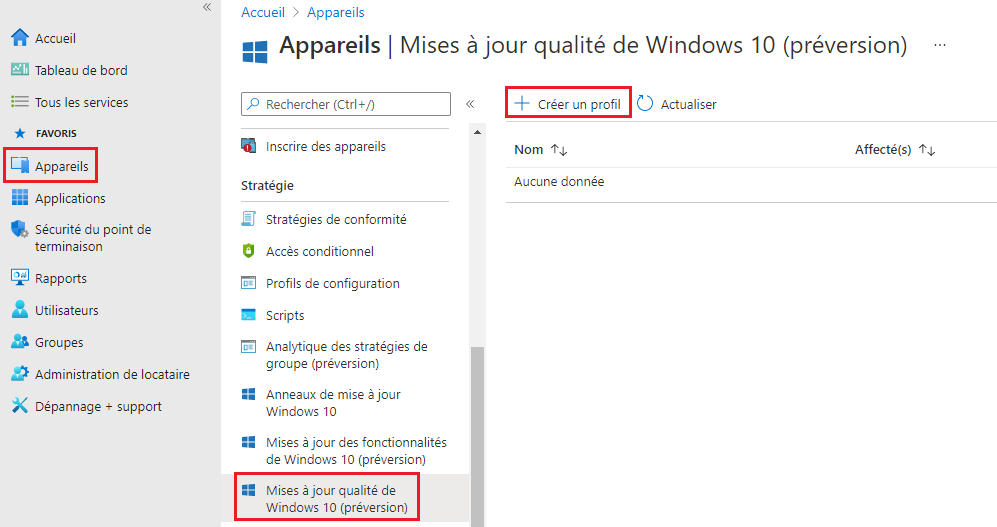
Creating a Windows 10 quality updates profile on Intune
A more efficient method is to create a Windows 10 quality update profile on Intune. This profile will speed up the installation of quality updates, such as the latest Tuesday patch or an out-of-band security update for a zero day exploit. To do this:
- Go to Endpoint and log in.
- Click on Devices and then Windows 10 quality updates (Preview).
- There, click on Create profile.
- Next, give the profile a name (Zero-day patches) and a description (Profile for deploying Zero-day patches)
- Then select the installation option including OOB (for Out-Of-Band) from the drop-down list.
- For the reboot application, you can stay on 1 day.
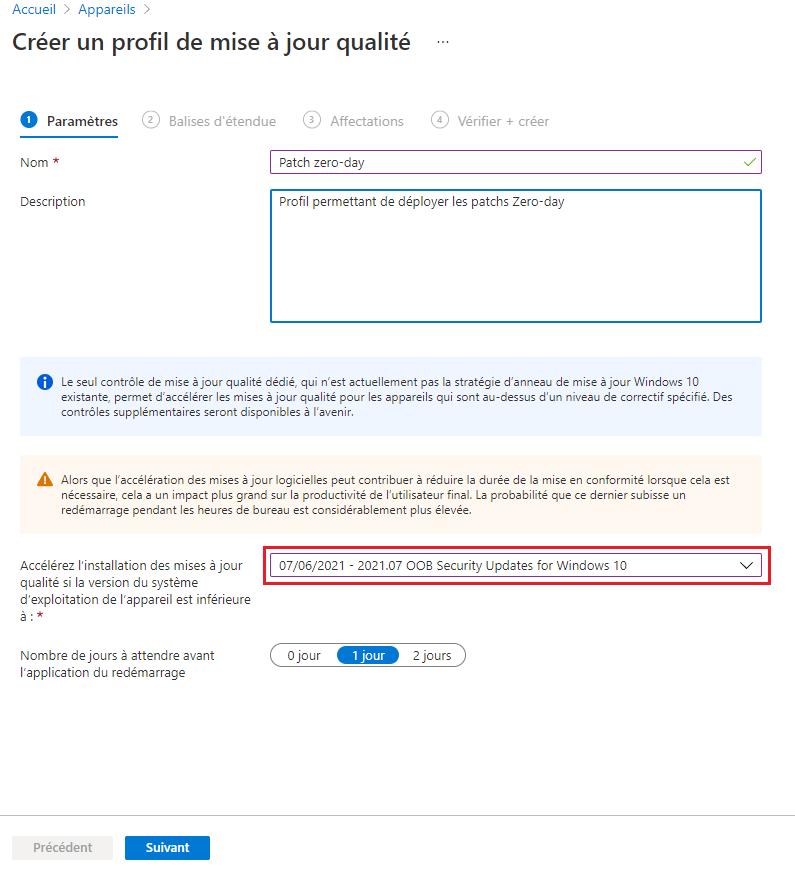
- Then choose the scope of this profile and the assignments.
- The creation wizard then summarises your choices, check and validate the creation.
When you return to the target machines, go back to Windows Update. The patches are correctly applied.