This article will allow you to perform an audit on the Local Machine Administrator group. This procedure is based on a custom WMI class, a configuration item and a configuration baseline.
You will need WMI explorer to validate your tests.
Implementing on a test machine
To begin, open a Powershell console in administrator mode. Copy and run the script below:
Note: if you want to run this script on a machine with an English OS, you need to modify line 213. You will need to replace ‘Administrators‘ with ‘Administrators‘ (or add it).
In order to check the correct execution of the script, launch WMI Explorer and follow the instructions on the image below:

The presence of the instances will confirm that the addition of the class is effective.
Extending the Hardware Inventory
On an SCCM console, go to “Administration“, then “Client Settings“. Open the default client properties. Then go to “Hardware Inventory” and click on the “Define Classes” button.
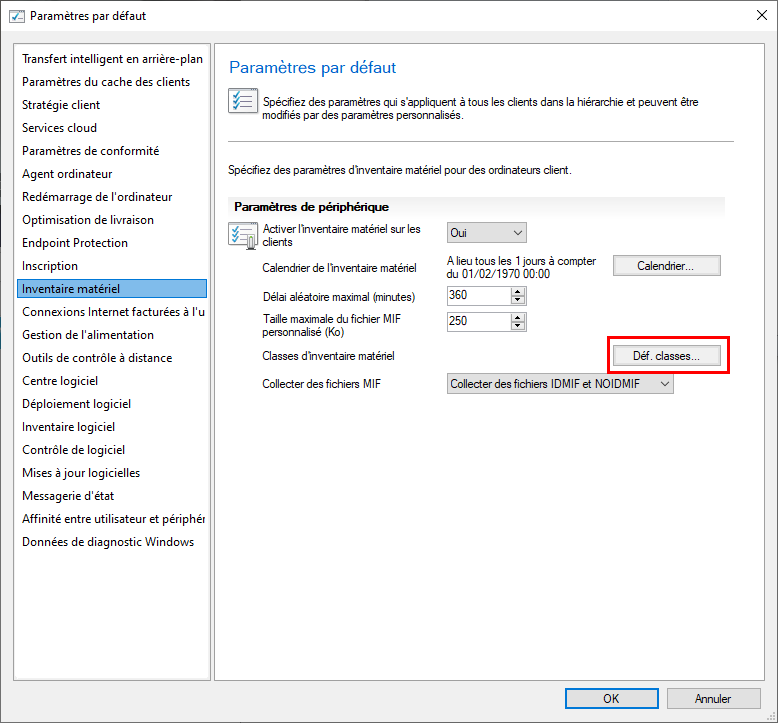
Then click on “Add“.
Connect the test machine and find the “LocalSecurityGroup” class. Select it and click ‘Edit‘. Check that everything is checked and then click OK until the default client properties are closed.
Creating the Configuration Item
Go to ‘Assets and Compliance‘, ‘Compliance Setting‘ and then ‘Configuration Items‘. Then click on ‘Create Configuration Item‘. Name it “Local Admin Inventory” and click “Next“.
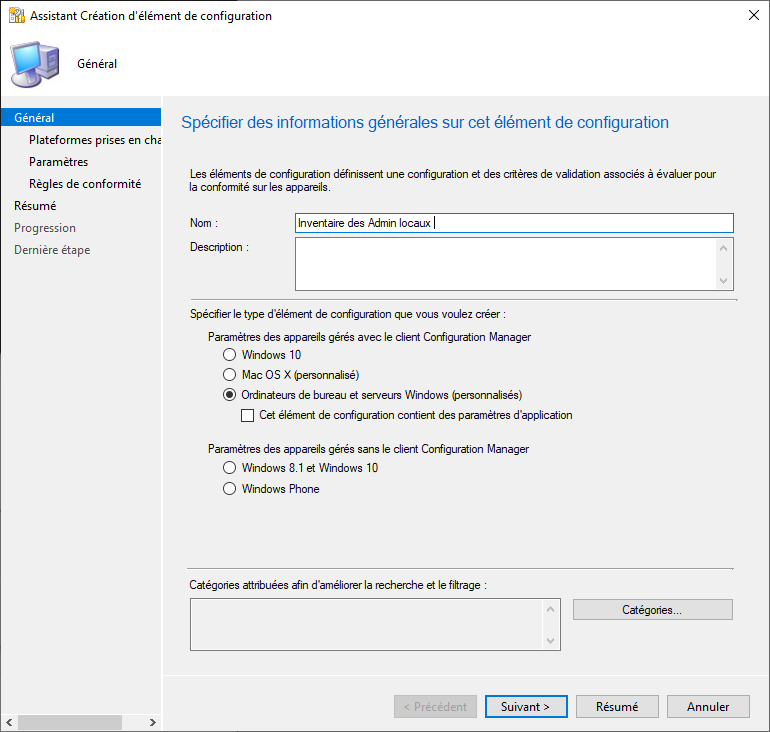
Check that all versions are selected.

Then click on “New“, a new window will appear. Name it “Compliance parameter” for example, choose “Script” as the parameter type and “Integer” as the data type. Then click on “Add Script“. Paste the script into the new window and click on “OK” and then “OK“. Then click “Next” to proceed to the compliance rules.

Then click on “New“. Name it “WMI Class Detection“. Then click on “Browse“. Choose “Local Admin Inventory” and click “Select“. Set the value to “0” and click “OK“.
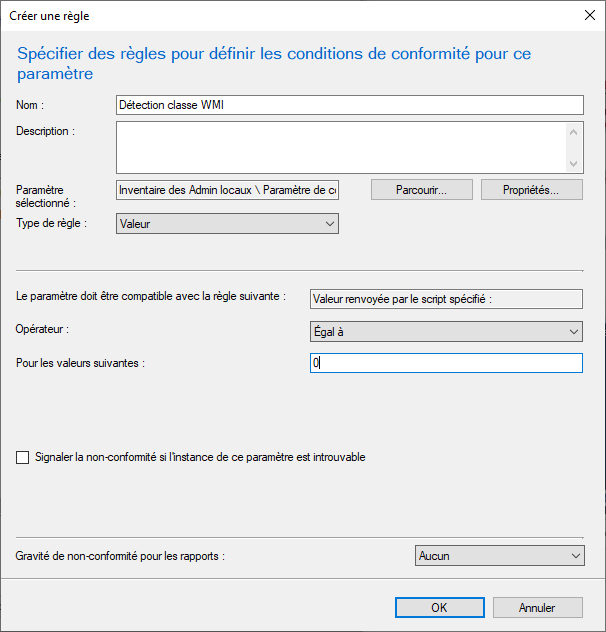
Finally, click on “Next” to access the summary, “Next” and “Close“.
Creating the configuration baseline
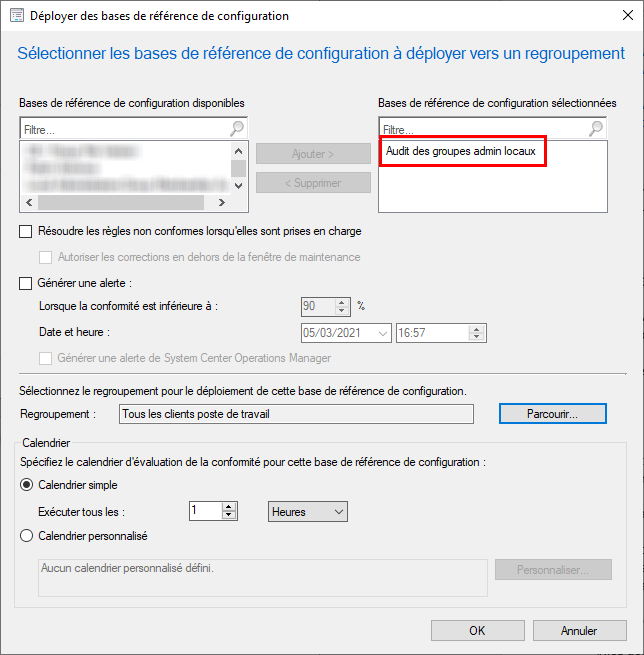
Go to “Assets and Compliance“, “Compliance Parameter” and then “Configuration Baseline“. Create a new configuration baseline and name it “Local Admin Group Audit“. Add the configuration item by clicking ‘Add‘. Select “Local Admin Inventory“, click “Add” and then “OK“. Click “OK” again to complete the configuration.

Next, right-click on “Local Admin Group Audit” and then click “Deploy“. Select the collection of computers you wish to target and adjust the frequency of assessment. Clicking “OK” will automatically start the deployment.
Reporting
Once the configuration baseline has been deployed, you can now move on to the reporting part. We will start with reporting from the console. To do this, go to “Monitoring“, then right click on “Queries” and select “Create a new query“.
Give your query a name (Local Admin Inventory), then click on “Edit Query Statement“. A new window will appear, click on the ‘View Query‘ button and copy and paste the query below:
select SMS_R_System.Name, SMS_G_System_LOCALSECURITYGROUPINVENTORY.Domain, SMS_G_System_LOCALSECURITYGROUPINVENTORY.User, SMS_G_System_LOCALSECURITYGROUPINVENTORY.SID from SMS_R_System inner join SMS_G_System_LOCALSECURITYGROUPINVENTORY
on SMS_G_System_LOCALSECURITYGROUPINVENTORY.ResourceID = SMS_R_System.ResourceId
where SMS_G_System_LOCALSECURITYGROUPINVENTORY.User not in ('AZOperator', 'azoperator', 'Exploit.Serveurs', 'vmoperator', 'admin.local', 'Administrateur', 'Admins du domaine')
order by SMS_R_System.Name, SMS_G_System_LOCALSECURITYGROUPINVENTORY.Domain, SMS_G_System_LOCALSECURITYGROUPINVENTORY.User
Click “OK” until all windows are closed. You will now have the complete list of local admins. You can also exclude some accounts to reduce the list.
It might also be interesting to create a report that can be sent regularly. Below is the SQL query to create it:
select
s1.Name0 as Nom, v_GS_LOCALSECURITYGROUPINVENTORY.Domain0 as [Domaine],
v_GS_LOCALSECURITYGROUPINVENTORY.User0 as [Utilisateur],
v_GS_LOCALSECURITYGROUPINVENTORY.SID0 as [SID],
csp.Version0 as [Modèle],
chas.ChassisTypes0 as [Type],
CASE
WHEN chas.ChassisTypes0 = 3 AND csp.Version0 = '7.0' THEN 'Virtual Machine'
WHEN chas.ChassisTypes0 in ('3','4','6','7','15') THEN 'Desktop'
WHEN chas.ChassisTypes0 in ('8','9','10', '17', '21') THEN 'Laptop'
END
from
v_GS_SYSTEM s1 left join
v_GS_SYSTEM_ENCLOSURE chas on chas.ResourceID=s1.ResourceID left join
v_GS_COMPUTER_SYSTEM_PRODUCT csp on csp.ResourceID=s1.ResourceID
inner join
v_GS_LOCALSECURITYGROUPINVENTORY
on
v_GS_LOCALSECURITYGROUPINVENTORY.ResourceID = s1.ResourceId
where v_GS_LOCALSECURITYGROUPINVENTORY.User0 not in ('AZOperator', 'azoperator', 'Exploit.Serveurs', 'vmoperator', 'admin.local', 'Administrateur', 'Admins du domaine')
order by
s1.Name0, v_GS_LOCALSECURITYGROUPINVENTORY.Domain0,
v_GS_LOCALSECURITYGROUPINVENTORY.User0
Credits :
https://mickitblog.blogspot.com/2016/11/sccm-local-administrators-reporting.html